How does AIM work?
AIM’s main function is to ensure the logical and physical access privileges associated with an employee’s role are always synchronized. This enables a company to ensure a person is physically present before permitting access to databases or applications. AIM supports all forms of business from multinationals with locations across the globe to multi-tenancy environments.
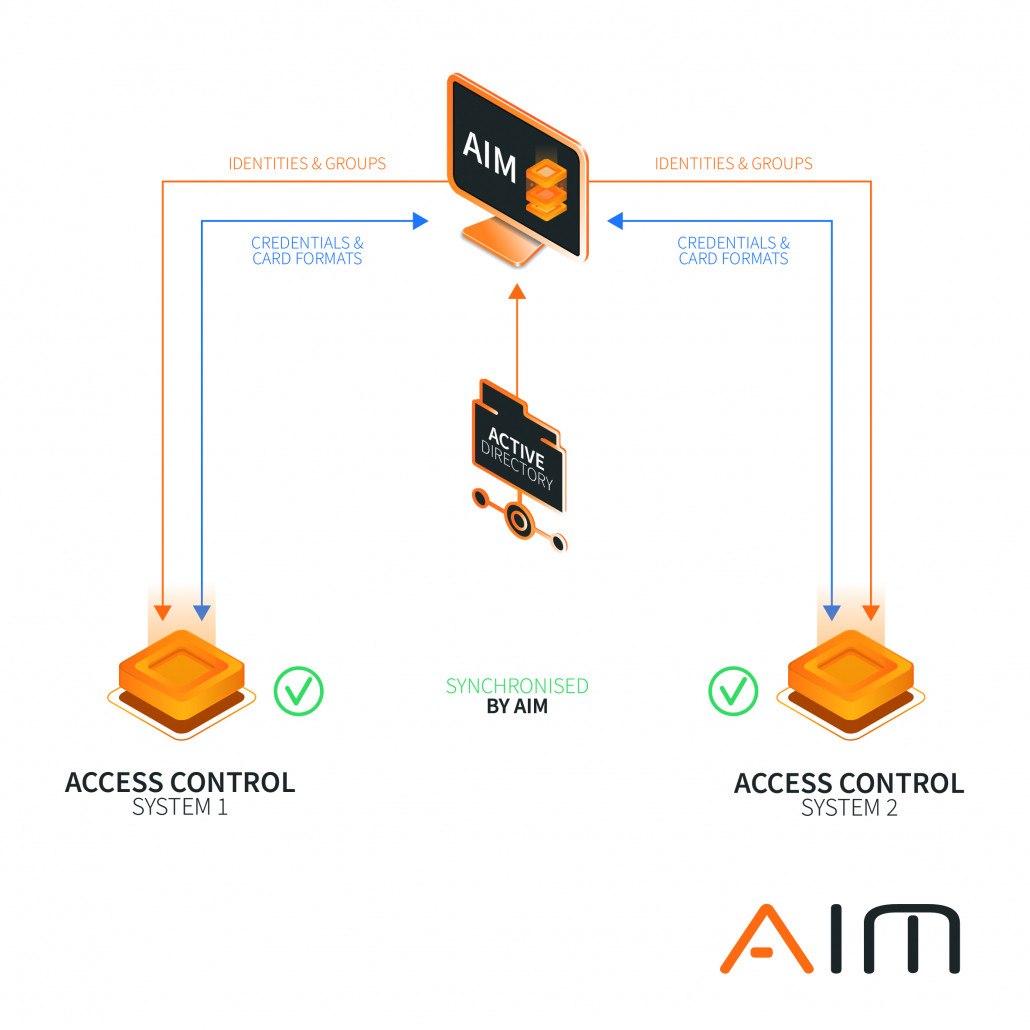
- Identities (cardholders/users) and group rights are taken from an authoritative data source here from the active directory Credentials (card information & formats) are shared between all systems
AIM advantages
ACCESS MANAGEMENT Ensuring the logical and physical access privileges associated with an employee’s role are always synchronized. This enables a company to verify a person is physically present before permitting access to buildings and assets.
INTEROPERABILITY AIM enables interoperability by automating the process of enabling access cards, cre[1]dentials or roles associated in one vendor’s access control system to be used at entry points associated with a different access control system or biometrics system.
USER EXPERIENCE Reducing multiple access cards for users and ensure correct access to privileged assets is assigned.
BUSINESS CONTINUITY Organisations can centrally manage access and quickly identify potential security threats related to duplicate badges and users. AIM also enables the continued use of existing access solutions without having to give up the advantages of unified processes and central data maintenance.
ADMIN EXPERIENCE The use of AIM and the associated harmonisation considerably reduces the administrative effort for the initial administration and the ongoing maintenance of user profiles and group rights.
Problems organisations face
- Users having multiple identities across security systems that do not communicate with each other.
- Multiple owners of a user’s identity in more than one access control system which can be amended, creating conflict without each owner being aware nor notified.
- Manual process to reconcile user’s multiple identities which have been created on more than one system in the same organisation.
- Changes that are made in one system are not registered in the other, resulting in a risk of users gaining unauthorised access
More info - CLICK HERE

