IPROTECT 10.3 - threat management
Everyday situations in various facilities have a huge impact on the security of people, property and data. They also ensure the smooth functioning of public administration bodies, various uniformed institutions, hospitals, entities responsible for producing and supplying us with energy, energy resources, fuels or access to IT services.
For this reason, the levels of threat management are a very important area not only for "risk managers" of commercial facilities, but also in the well-known facilities of critical infrastructure, which plays a huge role in the functioning of the state and the lives of its citizens, and protecting it is one of the most important goals facing the state.
This has given rise to the need to implement dynamically changing scenarios, including in access control systems, in case the threat level changes.
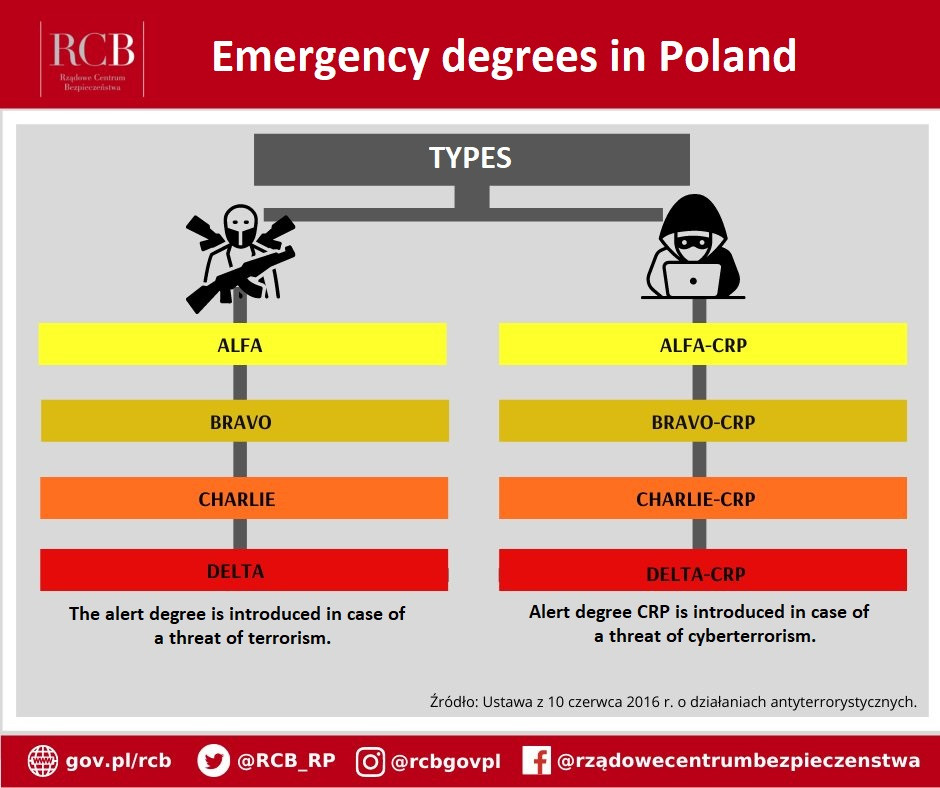
An extension of the above are CRP degrees, which are introduced in a terrorist threat situation. It applies to public administration ICT systems or systems that are part of critical infrastructure.
- First alert level (ALPHA-CPR)
- Second alert level (BRAVO-CPR)
- Third alert level (CHARLIE-CPR)
- Fourth alert level (DELTA-CPR

What are the types/levels/categories of threats in the facilities for which we will provide our solutions?
In critical infrastructure facilities, the types of threats are based on the Emergency Management Act
CATEGORY I - hazards resulting from natural disasters such as.
- Earthquake
- Drought
- Fire
- Reason
CATEGORY II - hazards related to human activity - deliberate e.g.
- Threats that are intentional human activity of a terrorist nature
- Threats that are economically and politically motivated
CATEGORY III - hazards related to human activity - UNINTENTIONAL e.g.
- Structural errors of facilities and installations that are elements of critical infrastructure
- Improper maintenance and operation of critical infrastructure facilities
In the area of citizen security in Poland, we have a law on anti-terrorist activities, which introduces a 4-stage system of alert degrees:
First alert degree (ALPHA)
Is introduced when information is received about the possibility of a terrorist event, the nature and scope of which is difficult to predict.
Second alert level (BRAVO)
Is introduced when there is an increased and predictable threat of a terrorist nature, but the specific target of the attack is not identified.
The third alert level (CHARLIE)
Shall be introduced in the event of an event confirming the probable purpose of a terrorist attack, harming security or public order, or the security of the Republic of Poland.
Fourth alert level (DELTA)
Is introduced in the event of an event of a terrorist nature causing a threat to security or public order, or the security of the Republic of Poland.
What can threat management look like in an access control system?
Using the "Threat Management" function, the way the access control system operates can be adjusted dynamically to the changing situation at the facility, such as:
- Whether to use a PIN in alarm mode?
- Change the normal operation mode of the reader (i.e., using an authorized card on the reader will unlock the passage) to "confirmation mode". That is, the opening of the passage will be possible through additional video verification of the operator or the card he used.
- The ability to block the access privileges of certain groups of people, e.g. guests, external workers, e.g. "production" workers at a chemical spill, only technical services have access.
What can be the "trigger" in the KD system for changing the threat level?
We have complete freedom, it can be:
- a contact input on the Orion door controller, e.g. an SOS button
- application of an access card with a special identifier
- a signal from a "third-party" system e.g. PSIM WinGuard or VMS VDG SENSE
- virtual button on the visualization of the IPROTECT system "KEYMAP"
What is our advantage?
- The ability to automate the way a facility operates in a systematic manner
- The ability to add multiple system operation scenarios to a single SKD system
- The ability to assign an individual maximum threat level for each person to access:
- Employee 1 - to level 1 only
- Employee 2 - up to level 4 max Flexibility
Building A
- The solution works on so-called areas/zones (AREA)
- In the IPROTECT system, each building, floor can be a separate zone/area
- The ability to assign an individual threat level to a zone/area means that in practice:- The entire building can be set to level 2
Building B - The first floor of Building B is to have a set level 1
- Floor 1 of Building B is to have a level 2 set up
- The server room, which is located in Building B on the 1st floor on to have a set level of threat 3
- The entire building can be set to level 2

